Edge Security Startups Driving Innovation for End Users
 By Michela Menting |
20 Oct 2021 |
IN-6319
By Michela Menting |
20 Oct 2021 |
IN-6319

Log In to unlock this content.
You have x unlocks remaining.
This content falls outside of your subscription, but you may view up to five pieces of premium content outside of your subscription each month
You have x unlocks remaining.
 By Michela Menting |
20 Oct 2021 |
IN-6319
By Michela Menting |
20 Oct 2021 |
IN-6319

Kameleon Security Launches Open Platform Approach to Hardware Security |
NEWS |
Kameleon is a semiconductor start-up, founded in 2019, working on developing an advanced hardware security platform known as the Security Processing Unit (ProSPU). It launched officially in July 2021. Targeted at servers, data centers, and cloud computing, the chip is a separate security processor that offers a hardware root of trust (based on Open Compute Project (OCP) security specification for Root of Trust): a compute platform with runtime security, which not only supports Kameleon applications, but has been built openly to also support third-party applications, and various crypto services (including key management) to securely store keys and data, and to provide a secure channel to cloud services.
Kameleon is one of many new startups focused on securing edge devices, a tricky task due to the breadth and variety of edge devices, from mobile to the Internet of Things (IoT). Other edge security startups focused in this space are those targeting security either specifically for constrained devices or for mid-range and smart devices. Several startups and companies focusing on constrained device security include the following:
- Check Point Software Technologies
- Red Balloon Security, Karamaba Security
- RunSafe Security
- Sternum
- Verimatrix
And for mid-range and smart device edge security, the following companies provide solutions:
- ProvenRun
- Qualcomm
- SiFive
- Trustonic
- ZAYA
The Rise of Security Processing Units and Edge Security Solutions |
IMPACT |
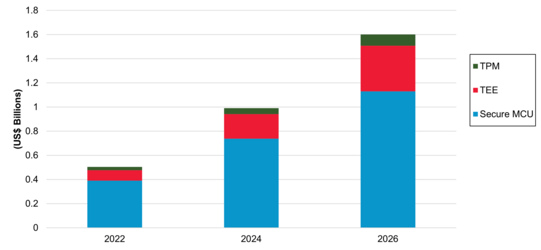
The security processor market is rarely qualified as a vibrant one, and solutions like those proposed by Kameleon are a breath of fresh air into an otherwise stagnant market. Until the advent of the Internet of Things (IoT), types and form factors remained pretty much aligned to their specific markets: Trusted Platform Modules (TPM) for PCs, Trusted Execution Environments (TEE) for smartphones and tablets, and secure integrated circuits for smartcards. But as connectivity and smart capabilities expand, so does the need for secure hardware to adapt outside of those traditional market applications, requiring these existing technologies to become more flexible: TPMs are targeting connected objects, TEEs targeting servers, dual-core capabilities in application processors, and even microcontrollers (one core for normal world functions, another for security), as well as crypto-processors and crypto-accelerators (both on-chip and alongside chip). While some of the existing standards bodies (such as the Trusted Computing Group and GlobalPlatform) have worked hard to expand the remit of their own security specifications, a flurry of security-focused silicon IP (such as Arm’s TrustZone) and proprietary processor solutions (e.g., Intel, Microsoft, AMD, Broadcom, Qualcomm, etc.) have emerged around them which have been relatively successful to date in the data center, PC, and mobile space, and are pushing ever further into the IoT space. The shipments of secure IoT edge devices with TPM, TEE, or Secure MCU capabilities are forecasted to grow globally from about half a billion USD in 2022 to $1.6 billion by 2026 (see chart below).
 |
The difficulty with IoT is the breadth and heterogeneous nature of its ecosystem. Attempts to develop a one-size-fits-all solution for hardware security is difficult. There are low-power, resource-constrained devices with little or no computation capabilities and other much smarter, multi-function, and well-resourced devices that are capable of many applications, and there is everything in between. With better edge processing capabilities, lower network latencies, expanded bandwidth, and greater cloud-based service opportunities, secure hardware technologies such as security processors are experiencing an unprecedented surge in demand. The gaps in the current market are driving innovation in the space.
The rise of open platforms, in particular, has really come to the fore in the last few years, with groups such as RISC-V and OPC, among others, working hard to democratize the security aspects of hardware to lower the barriers to entry for developers by reducing costs (notably as they relate to Information Protection Recovery (IPR) and licenses) and promoting interoperability. In large part, the “build-your-own-platform” mentality, which is greatly inspired by the maker movement, is increasingly targeting security technologies. As a result, the security industry is seeing a new breed of on-device edge security-focused startups that are offering one security element (such as a piece of code, a virtualization technology, etc.) which is not tied to any one system, but on the contrary, can run on a variety of different processors and platforms. The following briefly explains how 5 innovative startups are tackling edge security.
Edge Security Startup Example #1: RunSafe Security focuses on “immunizing” code bases for embedded and smart devices
Edge Security Startup Example #2: ProvenRun offers a trusted OS (TEE) and a secure software hypervisor for isolating an existing OS and the legacy software stacks in embedded connected devices.
Edge Security Startup Example #3: Sternum specializes in autonomous runtime protection and observability for IoT devices throughout the product life cycle.
Edge Security Startup Example #4: SiFive offers a low trusted computing base with roots of trust for SoCs, as well as a security model for isolated code execution and data protection.
Edge Security Startup Example #5: Zaya offers a secure embedded OS for the IoT that is ARM PSA-certified.
Kameleon goes a step further in that it provides the whole security processor, but it does not tie the user in with its own products at the application level (although that is an option). The user is free to use other third-party applications of their choice within that security processor.
Partnerships Key to Growth for Edge Security Startups |
RECOMMENDATIONS |
Edge security startups with aspirations of hitting it big can take a few hints from Kameleon, as the Israeli firm has taken the right steps toward success. Kameleon has ambitious plans for its ProSPU and will be targeting PC-based use cases followed by industrial, automotive, IoT, mobile, and critical infrastructure markets. The security startup has a partnership with Xilinx (who is also an investor) to secure Xilinx FPGAs. It has showcased a new project at the Open Compute Project (OCP) Global Summit in November 2021 on remote attestation for Xilinx’s peripherals. Its partnership with Xilinx is important; it provides both credibility and an opportunity to showcase what the technology can achieve more concretely. Other startups can also improve their capabilities and acquire new competencies through ecosystem alliances that are mutually beneficial for both parties.
But even if the use case is proven, edge security is always a difficult sell if the value of the technology is not translated to the eventual end-users. This is where clever marketing and educational campaigns have an enormous impact on the bottom line. Kameleon and other edge security startups will have to show not only that they can provide security, but also that they can create value and offer an attractive Return on Investment (ROI) for deployers.