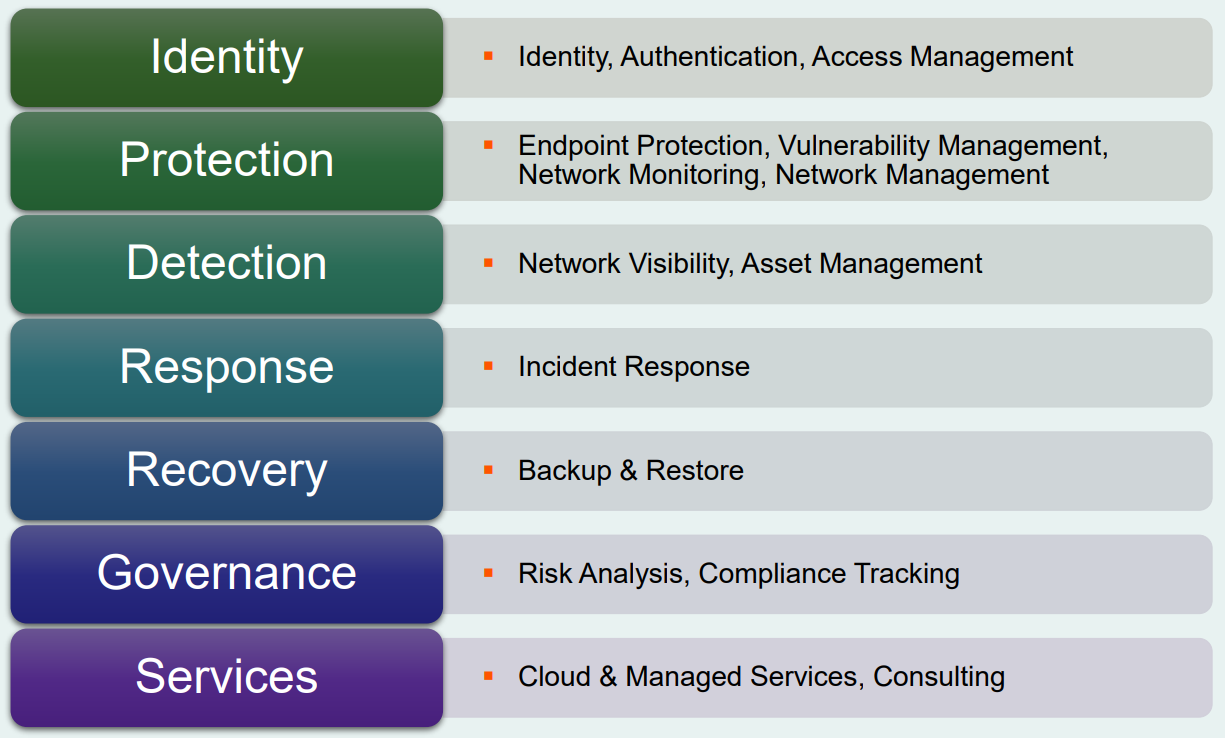
In the age of Industry 4.0 and digital transformation, the need for effective security solutions in industrial environments is made more apparent. As a result, cybersecurity spending for critical infrastructure will reach roughly US$126 billion by the end of the year, with Information Technology (IT) being the leading use case. While critical infrastructure—defense, energy, health, transport, etc.—has been the main adopter of industrial cybersecurity solutions, more sectors will begin to invest in security in an ever-connected world. There are seven areas of focus when it comes to solutions:
- Protection
- Detection
- Services
- Identity
- Governance
- Response
- Recovery
While protection and detection are the most mature markets, services and identity are on the fast track to becoming fully fledged. But the last three areas of focus—response, recovery, and governance—have lagged behind. It’s worth assessing these three areas as industry players aren’t as exposed to the associated technologies but could surely benefit from them.
Figure 1: A Visual Showcasing of the Seven Industrial Cybersecurity Solutions (Source: ABI Research)
Response
Response technologies empower users to contain cybersecurity threats in real time, allowing industrial players to fix security issues before they become a pervasive problem that could compromise the company. Although this is a much-needed solution, the response market is still quite small in critical infrastructure, because it was just introduced to industrial applications only a few years ago. Currently, a lot of attention is being paid to faster threat detection Machine Learning (ML)/Artificial Intelligence (AI) for automation, toward which early adopters have gravitated.
Some of the technology solutions that are maturing for industrial security response are Information Security Management Systems (ISMSs), incident databases, and attacker research/monitoring. Then, there are also several emerging solutions, such as crisis management, incident response team creation, data forensics, notification procedures, and eradication, among others.
On the downside, incident response services are expensive and not bulletproof; occasionally, false positives may be issued in environments that have a high number of IIoT and connected Operational Security (OT) devices. Plus, if response services require manual intervention, this opens the door to more errors. According to the World Economic Forum, 95% of cybersecurity issues are the result of human error.
A handful of vendors in the incident response space include the following:
Recovery
Sometimes, organizations are hit with cyberattacks, despite having security solutions in place. As found in Deep Instinct’s Voice of SpecOps 2022 report, nearly half (47%) of cybersecurity professionals believe it’s impossible to prevent every threat. It’s imperative that critical infrastructure has a “Plan B” for when an attack does occur.
Cyber resilience is the chief selling point for recovery technologies, as it supports Business Continuity and Disaster Recovery (BCDR). The recovery market has been mostly concentrated on data backup and recovery; however, process and operational backup are bound to become attractive features in the coming years. Keeping the flow of operations moving in the wake of an attack reduces, or completely eliminates, the financial impact of a security breach. A few promising use cases on the horizon are offline backups, business impact analysis, and recovery metrics tracking.
The challenges that come with recovery solutions are ensuring infrastructure functionality and physical safety when activating the recovery system, defining the exact business benefits of investing in the technologies, and designing timely and unembellished recovery systems for ICSs and Supervisory Control and Data Acquisition (SCADA) systems.
The ensuing five vendors provide industrial recovery solutions:
Governance
Security governance is used to regulate organizations' security apparatuses, which provides clear guidance on how to mitigate threats. Even though governance has been available for a long time in critical infrastructure and highly regulated industries, it’s still a niche offering. However, as non-regulated sectors expand their Industrial Internet of Things (IIoT) tech stack, governance and standardization will branch off to these other sectors. Some of the trends surrounding governance are security by design, third-party risk assessment, plans for security guarantees and cyber insurance, and new means of reporting for Chief Information Security Officers (CISOs).
One of the main challenges facing governance implementation is the fact that there are still some unknowns associated with Industrial Control Systems (ICSs) and data risk analysis. Another challenge is the ecosystem—with multiple vendors involved in a sophisticated supply chain. Finding a way to account for various technologies and vendors can make consistent governance and standardization a difficult endeavor.
The following are several vendors that provide governance solutions:
A Broader Market
Historically, cybersecurity spending has mainly been reserved for critical infrastructure in attempts to thwart attacks from state-sponsored actors. But as Industry 4.0 and the subsequent digital transformation take shape, industrial cybersecurity is extending to other sectors. Governance, response, and recovery—the solutions explored in this blog post—are just three of seven important areas of focus when it comes to industrial cybersecurity.
To learn more about these three markets and the four remaining industrial cybersecurity markets, download ABI Research’s A Blueprint of Security Solutions for Industry 4.0 presentation. This research is part of the company’s Industrial Cybersecurity and Industrial & Manufacturing Research Services.

