The need for a reliable IoT device management solution has never been more apparent than now. During the pandemic, the frequency of cyberattacks reached unprecedented levels. In every corner of the digital world, there’s a cybercriminal lurking in the virtual shadows. In fact, Cybersecurity Ventures predicts that cybercrimes will cost businesses US$10.5 trillion per year by 2025. With the ever-growing uneasiness of digital security, organizations are rethinking how vulnerable their Internet of Things (IoT) devices may be to a breach. Not only would an IoT attack result in the loss of financial capital and confidential information, but also the loss of trust in the market.
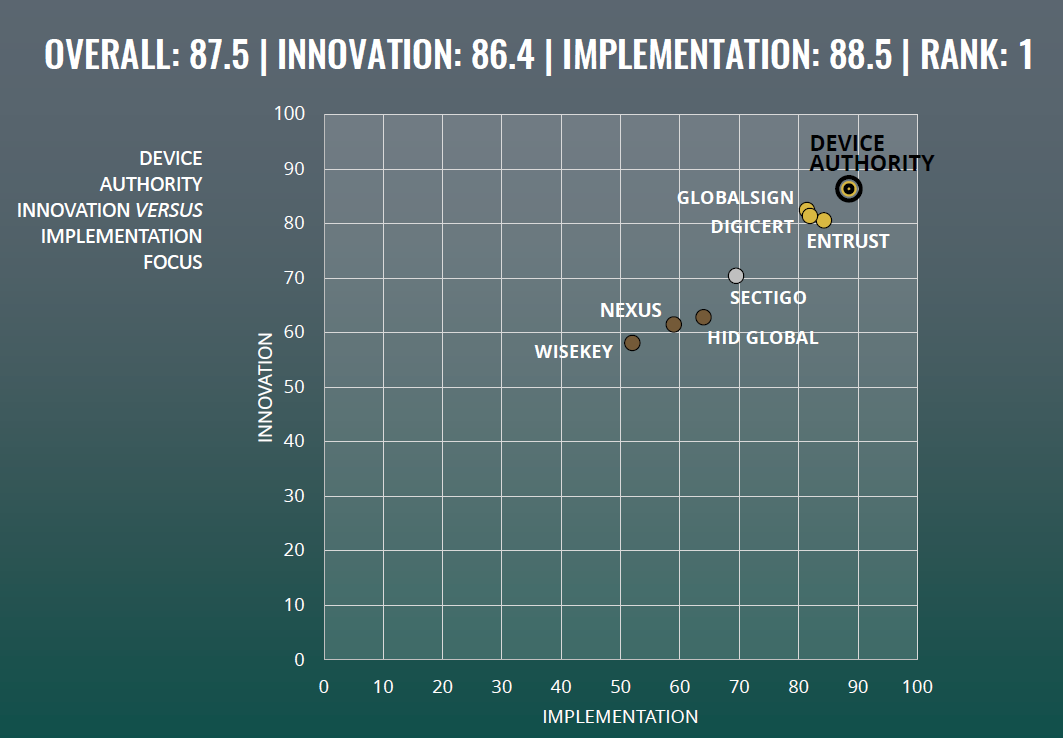
Of course, to mitigate the threat of IoT attacks, organizations must turn to effective security solutions for proper IoT device management. Recently, ABI Research compiled an in-depth competitive rankings report of eight IoT security providers and Certificate Authorities (CAs): Entrust, Device Authority, GlobalSign, DigiCert, Sectigo, HID Global, Nexus, and WiseKey. Our analysts looked at each company’s implementation and innovation.
Device Authority came in at the top for both categories. Given its outstanding position in the IoT security market, it’s worth taking a closer look at what makes Device Authority so practical—and what features organizations look for in their IoT device management tools.
IoT Device Management Starts at the Implementation
Our analysts ranked a company's implementation on the following: designs, pricing, ID provisioning, and ID management.
Design
Device Authority’s flagship IoT device management platform is KeyScaler, which is a highly personalized option for clients because of the various deployment options available (on-premises, hybrid, cloud, and Software-as-a-Service (SaaS)).
Flexibility is also extended to the integrations side of IoT device management. With KeyScaler, developers can integrate with client Software Development Kits (SDKs), development libraries, sample scripts, and even source code developed by Device Authority itself. Moreover, third-party applications and platforms,like Microsoft Azure, PTC, ThingWorx, and Amazon Web Services (AWS) IoT are fully compatible with KeyScaler.
Pricing
The pricing model that Device Authority uses consists of a base annual licensing fee for access to the platform, plus an annual subscription fee per device. With this pricing model, customers have access to a solution tailor-made for their organization’s needs.
ID Provisioning
Device Authority offers a full-cycle solution for ID provisioning—from injection to issuing security certificates throughout the IoT device's lifecycle. To address the difficulty in preventing IoT attacks stemming from brownfield deployments, Device Authority offers a cryptolibrary named Dynamic Device Key Generation (DDKG), which does away with reliance on a secured enclave or a Trusted Platform Module (TPM). Plus, it can prevent key theft by using sophisticated encryption.
It should be noted that Device Authority’s ID provisioning is best served during the manufacturing stage of an IoT device. It is geared toward the management of high-end IoT devices within the realm of the company's main target markets: industrial, enterprise, healthcare, manufacturing, and automotive.
ID Management
Instead of requiring an IoT device birth certificate for identification, Device Authority can mark a device’s identity using static credentials, manufacturing numbers, serial identities, and other forms of identity. In turn, a device can onboard with KeyScaler and remain trackable throughout its lifecycle. If any device behavior indicates a possible IoT attack, KeyScaler is in positon to pick up on it.
ID management is simple with Device Authority. KeyScaler allows the management of IoT devices from any facet of the system—thanks to its REST Application Programming Interfaces (APIs). An attractive feature of KeyScaler is its ability to operate alongside most chipsets on the market. For organizations hoping to prevent attacks on their IoT devices, they’ll find value in KeyScaler’s ability to provide Public Key Infrastructure (PKI) certification, tokens, secure code signing, and key management.
Using Innovation to Tackle IoT Attacks
Our innovation rankings stemmed from the following criteria: deployment, automation, IoT participation, and ecosystem partners.
Deployment
To connect to existing IoT devices, Device Authority offers integration between client-side SDKs and server-side APIs. Much of the company’s IoT device management platform innovation comes from Hardware Security Modules (HSMs) via third-party integrations, so that customers can add another layer to their IoT security apparatus.
Device Authority also supports edge-based compute, so that infrastructure without a steady Internet connection, such as hospitals and factories, can manage their IoT devices.
Automation
To make deployment and scalability optimal, onboarding is policy-driven and automated. The way that Device Authority’s deployment model and architecture are designed, organizations of all sizes have an easy path to scaling. And because of the platform’s use of edge security, this provides IoT devices under private edge server environments with automated protection from IoT attacks.
IoT Participation
With 10 issued patents, it’s clear that innovation is a keystone of Device Authority’s business model. Some notable patents from the company's IoT management platform are:
- Tamper-proof credential management
- Security extension to offline IoT devices
- Automated PKI management and access control
- Network and communication protocol agnosticism
Ecosystem Partners
HSM providers/CAs, application vendors, chipset manufacturers, and secure supply chain vendors are all on the list of ecosystem partners that Device Authority has established. Moreover, Device Authority allows customers to integrate with third-party platforms and CAs, which provides a great deal of flexibility for IoT device management.
Device Authority’s KeyScaler Ready program harnesses partnerships with vendors across multiple verticals. Some notable vendor partners include Ericsson, BSI, Microsoft Azure IoT, and Venafi, among others.
What Can We Learn from Device Authority's IoT Device Management Solutions?
As we found in last year’s Connected & Protected: The Vulnerabilities And Opportunities Of IoT Security whitepaper, there will be 23 billion connected IoT devices by 2026. This presents an enormous market opportunity for vendors as security challenges continue to emerge.
The breakdown of Device Authority’s technology serves as a solid baseline for security providers and CAs that want to provide innovative IoT device management solutions. The takeaway from the analysis is that a customer-first approach—in tandem with a healthy dosage of industry partners and proprietary technologies—ought to be the main priority for vendors.
To dig deeper into how Device Authority and other vendors help companies circumvent IoT attacks—and to see the full competitive rankings ABI Research compiled—download the IoT Device Identity Lifecycle Management competitive assessment (CA-1333). This report is part of the company’s IoT Cybersecurity research service, which includes research, data, and ABI Insights.

